Email is widely used in both business and personal contexts, but its communications are exposed to various security risks. To address these risks, various authentication and encryption technologies are employed for sending and receiving email.
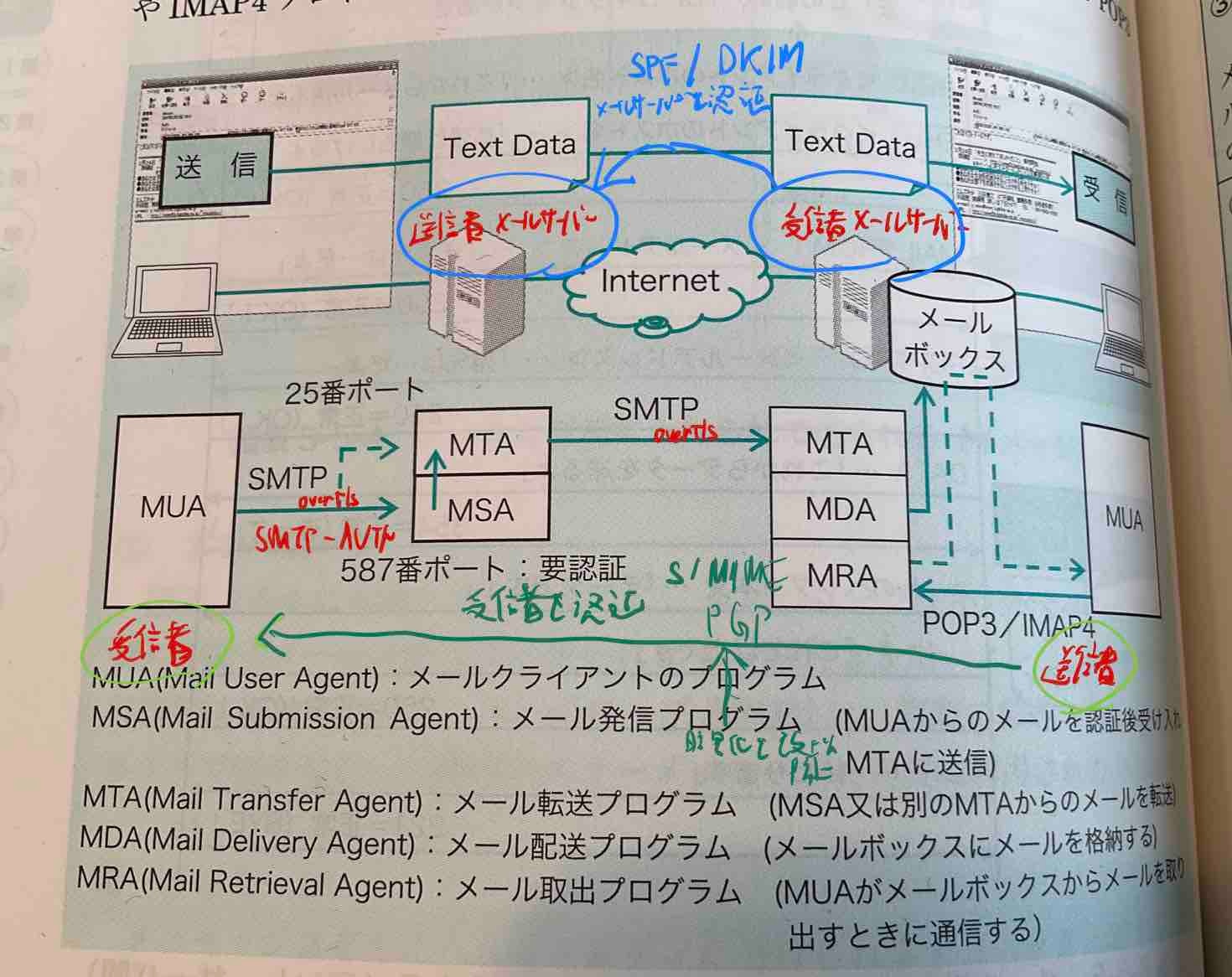
1. Communication Path Encryption
SMTP (Simple Mail Transfer Protocol) over TLS
SMTP is the protocol used for sending email, but by default, communication content is sent in plaintext. By using TLS (Transport Layer Security), SMTP communication can be encrypted, preventing eavesdropping and tampering by third parties on the communication path.
- Note: TLS encryption is limited to protecting the communication path. Once the email reaches and is stored on the destination mail server, it is decrypted, so it cannot protect against unauthorized access to the mail server itself.
2. Sender Mail Server Authenticates the Sender
SMTP Auth (SMTP Authentication)
SMTP Auth is a mechanism where the mail server authenticates that the sender (user) is a legitimate user when sending email. It uses username and password for authentication, preventing unauthorized users from using the mail server.
- Authentication Method: Secure authentication methods that do not directly transmit the password, such as challenge-response, are often used.
3. Receiving Mail Server Authenticates the Sending Mail Server
These technologies aim to prevent sender domain spoofing (spoofed emails).
SPF (Sender Policy Framework)
SPF is a mechanism that verifies whether the source IP address of an email is from a legitimate sending server for that domain.
- How it works: An SPF record listing the IP addresses authorized to send email is registered in the DNS server of the sending domain. When the receiving mail server receives an email, it queries the DNS for the SPF record of the sending domain and checks whether the source IP address matches the IP addresses listed in the SPF record.
- Method: IP address-based authentication.
DKIM (DomainKeys Identified Mail)
DKIM is a mechanism that attaches a digital signature to an email to verify that the sending domain is legitimate and that the email content has not been tampered with.
- How it works: The sender hashes parts of the email header and body, signs them with their private key, and attaches the signature to the email. The corresponding public key is registered in the DNS server of the sending domain. When the receiving mail server receives an email, it retrieves the public key from the sending domain’s DNS and verifies the signature with that public key.
- Method: Digital signature method.
4. Recipient Authenticates the Sender and Protects Email Content
These technologies aim to authenticate the email sender and protect the confidentiality and integrity of the email content.
S/MIME (Secure / Multipurpose Internet Mail Extensions)
S/MIME is a standard technology that uses public key cryptography to perform digital signatures and encryption on emails.
- Digital Signature: Proves the sender’s identity and detects email tampering.
- Encryption: Encrypts email content so that only the recipient can read it.
Using S/MIME requires a digital certificate issued by a trusted Certificate Authority (CA).
PGP (Pretty Good Privacy)
PGP is software that uses public key cryptography to perform digital signatures and encryption on emails, similar to S/MIME.
- Feature: While S/MIME uses a hierarchical trust structure through certificate authorities, PGP adopts a decentralized trust model called the “Web of Trust.”
- Usage: The sender and recipient need to exchange public keys in advance.
By combining these technologies, email communication security can be strengthened in multiple layers, reducing risks such as phishing scams, spam, and information leakage.